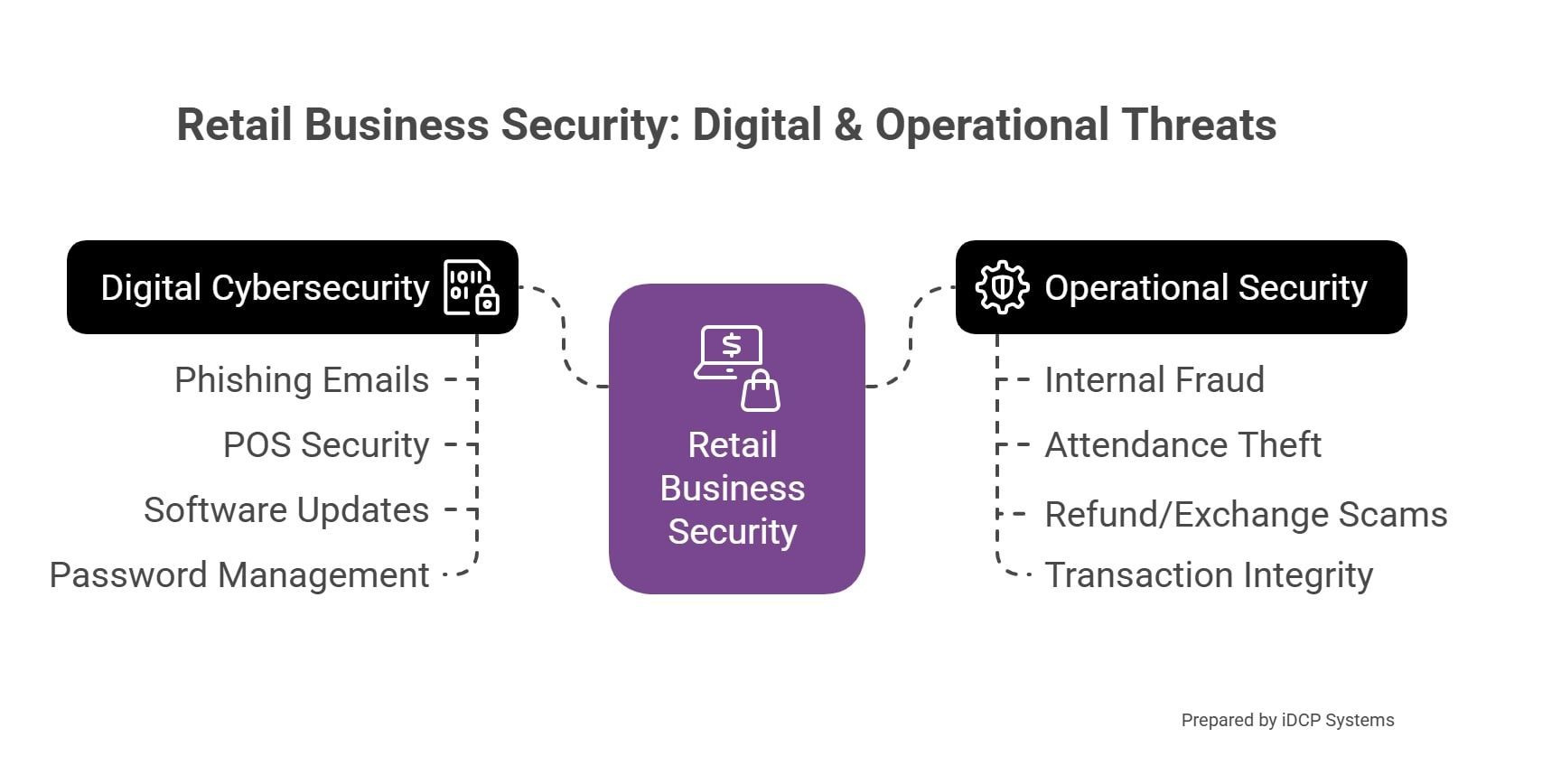
As retail businesses grow more digital, they also become more vulnerable to hidden threats- from system breaches to ransomware attacks. These dangers not only affect sales but can also damage your brand and customer trust.
At iDCP, we’ve worked with many retail and distribution companies to secure their operations through technology.
Here are 8 practical steps you can take to protect your business- and we’ve included expert backup strategies to help you recover quickly if the worst happens.
1. Update Your Systems Regularly
Beyond simply keeping your systems current, this is a proactive defense against
known vulnerabilities. When software developers find a security flaw, they release a patch to fix it. Delaying these updates leaves a digital "back door" open for hackers.
This applies to every piece of technology you use, from your
ERP and POS systems to your web browser and even your employees' smartphones. By making a regular schedule for updates, you ensure that your business is always protected against the latest security threats.
2. Implement Proper User Access Controls
In a retail environment, not every employee needs access to all your business data. A cashier doesn't need to view sensitive financial reports, and a sales associate shouldn't be able to change inventory prices. By implementing
role-based permissions, you ensure that staff members can only access and modify the data essential to their job.
This reduces the risk of both malicious activity and human error. It also makes it easier to track and audit who has accessed specific data, creating a clear chain of accountability.
3. Backup Your Data – The Right Way
Backing up your data is not enough. You need a reliable and secure backup strategy such as 3-2-1-1 backup method:
- 3 copies of your data
- 2 different storage media (e.g., local drive + cloud)
- 1 copy stored off-site
- 1 immutable copy (cannot be altered or deleted)
Immutable backups are critical for ransomware protection. This ensures that even if a hacker gains access to your network, they can't corrupt your backups.
4. Secure Your Network
Your business network is the highway for all your data, and it needs to be protected from unauthorized access. A strong
firewall acts as a security guard, monitoring and controlling incoming and outgoing network traffic. Using
strong Wi-Fi encryption (WPA3) prevents attackers from easily snooping on your data.
For employees who need to access the network remotely, a
VPN (Virtual Private Network) provides an encrypted "tunnel," ensuring that their connection is secure and private..
5. Train Your Employees
Human error is one of the top causes of security breaches. Train your staff to:
- Spot phishing emails
- Avoid using weak passwords
- Report suspicious activity immediately
Ongoing awareness can prevent costly mistakes.
6. Use Strong Passwords and Multi-Factor Authentication (MFA)
A simple, easy-to-guess password is an open invitation for a data breach. Implement a policy that requires employees to use
strong, unique passwords for all business accounts. Better yet, enforce the use of
Multi-Factor Authentication (MFA).
This requires a second form of verification, such as a code sent to a mobile device or a fingerprint scan, in addition to a password.
Even if a hacker steals a password, they will be unable to access the account without the second factor.
7. Monitor for Suspicious Activity
Being proactive is the key to catching a threat before it becomes a full-blown crisis.
Set up monitoring systems to look for
unusual login attempts, such as someone trying to log in from a different country or at an odd hour.
Also, watch for
unusual file changes or large spikes in network traffic, as these can be signs of malware or a data exfiltration attempt.
Early detection allows you to respond quickly and minimize the damage.
8. Adopt a Cloud-Based ERP with Built-In Security
Managing security can be complex, and a modern
cloud-based ERP system like iDCP can do much of the heavy lifting for you. These platforms are designed with security in mind, often including
end-to-end encryption of your data as it moves between devices.
They also handle regular software updates and backups automatically, reducing the burden on your team. This allows you to focus on growing your business with the peace of mind that your data is protected by industry-leading security experts.
Know How Ransomware Works
Ransomware encrypts your company’s data and demands payment in exchange for a decryption key.
Without a backup, especially an immutable one, you may lose access to customer data, inventory records, and financial documents permanently.
Being prepared with the right strategy is your best defense.
Final Thought
You don’t have to wait until something goes wrong to take action.
The right combination of technology, training, and backup strategy can keep your retail operations safe from hidden threats.
While some providers focus solely on delivering a functional system, we believe in a higher standard. At iDCP, we design our ERP solutions with security in mind- from user access controls to cloud backups, so
we can empower our clients to run their business with confidence.
Ready to transform your business with iDCP Systems?